Regional security might sound like an old story of border disputes and military standoffs, but the reality in 2025 is anything but familiar. Over 60 percent of major threats now come from hybrid and technological sources instead of traditional military force. So, while everyone is focused on tanks and treaties, the biggest risks are coming from quantum code, digital sabotage, and shifting alliances that never make the headlines.
Table of Contents
- Understanding Regional Security Dynamics Today
- Major Actors And Evolving Threats In 2025
- Regional Security Complex Theory Explained
- Policy Options And Future Scenarios
Quick Summary
| Takeaway | Explanation |
|---|---|
| Evolving Geopolitical Landscape | The contemporary security environment is influenced by technological advancements, shifting alliances, and emerging non-state actors, requiring a reassessment of traditional military paradigms. |
| Importance of Technological Resilience | Cybersecurity and protection of critical infrastructure are paramount, as the lines between physical and digital security have blurred, necessitating adaptive security frameworks. |
| Hybrid Security Challenges | The emergence of hybrid and asymmetric security threats requires nations to implement flexible response mechanisms, integrating technological, economic, and social strategies for effective security management. |
| Regional Security Complex Theory (RSCT) | RSCT offers an analytical framework to understand complex regional interactions and security interdependencies, enhancing comprehension of contemporary security dynamics beyond state-centric views. |
| Need for Adaptive Policy Frameworks | Policymakers must develop proactive, interdisciplinary policy strategies that can swiftly address and adapt to the rapidly evolving security landscape, emphasizing flexibility and collaboration. |
Understanding Regional Security Dynamics Today
Regional security dynamics represent a complex and multifaceted landscape of strategic interactions, geopolitical tensions, and evolving power relationships that shape global stability. These dynamics are increasingly characterized by interconnected challenges that transcend traditional geographical boundaries and demand sophisticated analytical approaches.
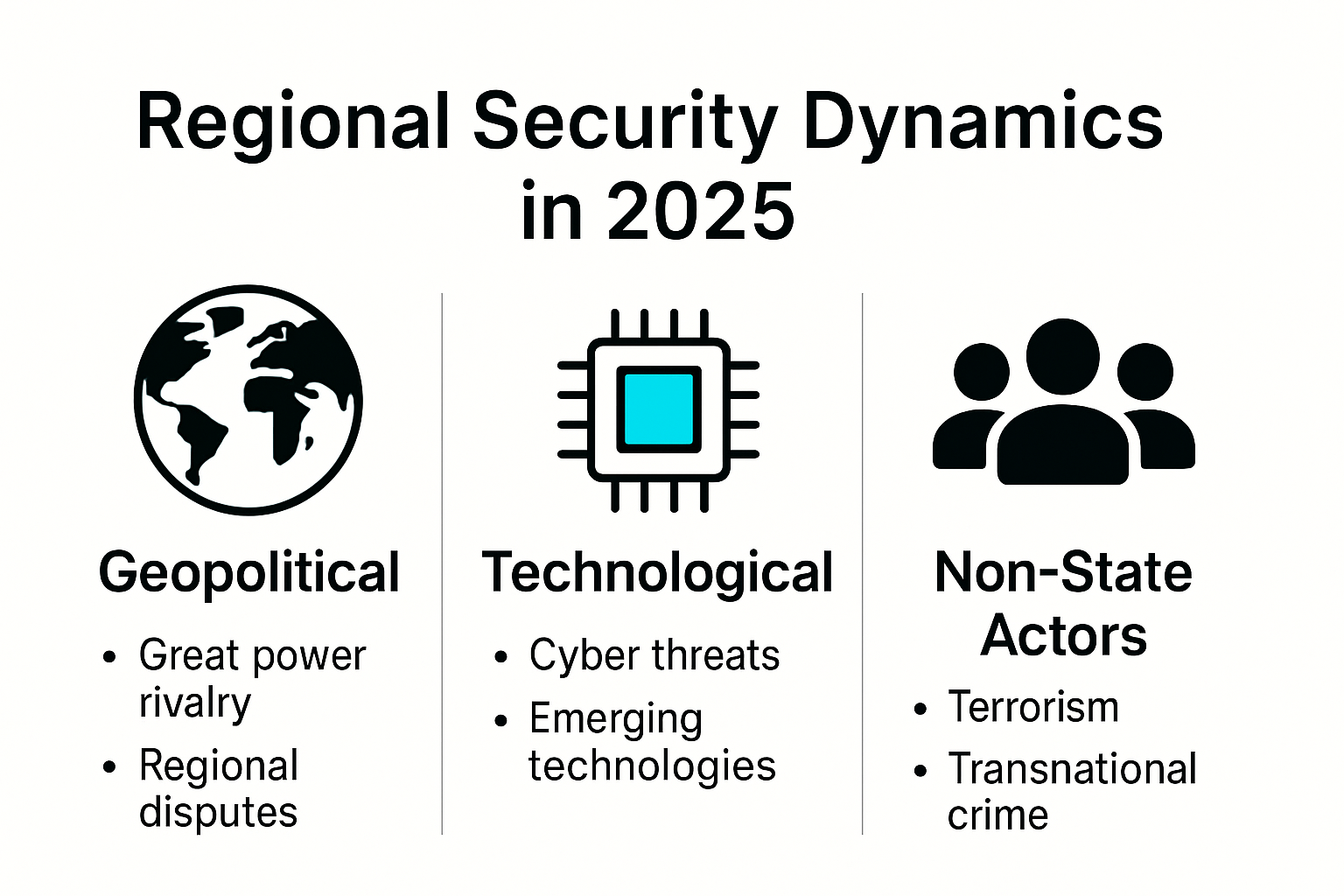
Emerging Geopolitical Complexities
The contemporary global security environment is marked by profound transformations driven by technological advancements, shifting alliances, and emerging non-state actors. Strategic competition has moved beyond conventional military paradigms, encompassing domains like cyber infrastructure, economic networks, and information warfare. Read our strategic analysis on emerging global tensions reveals how traditional security frameworks are being fundamentally restructured.
Modern regional security dynamics are increasingly influenced by asymmetric threats, technological disruptions, and complex interdependencies between state and non-state actors. The proliferation of advanced technologies such as artificial intelligence, quantum computing, and sophisticated communication networks has dramatically altered strategic calculations. National security strategies must now account for multidimensional challenges that cannot be addressed through traditional military approaches alone.
Technological Disruption and Security Challenges
According to Carnegie Endowment for International Peace, technological disruption is fundamentally reshaping security paradigms. Cybersecurity has emerged as a critical domain where state and non-state actors engage in continuous strategic competition. The boundaries between physical and digital security have become increasingly blurred, requiring comprehensive and adaptive security frameworks.
Critical infrastructure protection, information warfare, and technological resilience have become paramount considerations in contemporary regional security strategies. Governments and strategic institutions must develop robust mechanisms to anticipate, detect, and respond to emerging technological threats that can potentially destabilize entire socio-political systems.

Strategic Adaptation and Resilience
Successful navigation of regional security dynamics demands continuous strategic adaptation and comprehensive understanding of evolving geopolitical landscapes. This requires interdisciplinary approaches that integrate insights from international relations, technological innovation, economic trends, and cultural dynamics.
The ability to develop flexible, responsive security architectures capable of addressing multifaceted challenges will be crucial for national and regional stability. Policymakers and strategic planners must cultivate advanced analytical capabilities, promote international cooperation, and invest in developing adaptive technological infrastructures that can effectively respond to emerging security threats.
Understanding regional security dynamics is no longer about understanding military capabilities alone but comprehending the intricate web of technological, economic, and social interactions that shape global strategic environments. As the world becomes increasingly interconnected, the complexity and sophistication of security challenges will continue to evolve, demanding equally sophisticated and nuanced strategic responses.
Major Actors and Evolving Threats in 2025
The global security landscape in 2025 is characterized by complex interactions between state and non-state actors, with emerging technological capabilities and asymmetric threats reshaping traditional strategic paradigms. Understanding the key players and potential security challenges requires a nuanced analysis of geopolitical developments and evolving strategic capabilities.
Here is a table summarizing the major actors and the types of threats they present in 2025 as discussed in this section.
| Actor Type | Capabilities/Threats | Strategic Focus |
|---|---|---|
| State Actors | Advanced weapons systems, cyber capabilities | Strategic competition, tech innovation, diplomacy |
| Non-State Actors | Cyber attacks, terrorism, tech-enabled disruption | Destabilizing national infrastructure |
| Emerging Powers | Investing in military, economic, and tech capacities | Regional influence, complex power dynamics |
| Cybercriminal Groups | Sophisticated network attacks, info manipulation | Undermining security, exploiting vulnerabilities |
State Actors and Strategic Transformations
Major global powers are increasingly investing in advanced technological capabilities that redefine military and strategic potential. Explore insights on strategic military technologies reveals how nations are developing sophisticated weapons systems and cyber capabilities that fundamentally alter strategic calculations.
According to RAND Corporation, state actors are experiencing significant shifts in power dynamics. Nations like China, Russia, the United States, and emerging regional powers are engaged in complex strategic competitions that extend beyond traditional military domains. These competitions now encompass technological innovation, economic networks, information warfare, and diplomatic influence.
Technological and Non-State Threat Landscapes
The proliferation of advanced technologies has empowered non-state actors to challenge traditional security frameworks. Cybercriminal networks, terrorist organizations, and decentralized technological groups now possess capabilities that can potentially destabilize entire national infrastructures.
Emerging technological domains such as artificial intelligence, quantum computing, and advanced communication networks have created unprecedented vulnerabilities. According to Carnegie Endowment for International Peace, these technologies enable sophisticated attacks that can compromise critical infrastructure, manipulate information systems, and undermine national security mechanisms.
Hybrid and Asymmetric Security Challenges
Contemporary security threats are increasingly characterized by hybrid and asymmetric approaches that blur traditional boundaries between military and civilian domains. State and non-state actors are developing sophisticated strategies that combine technological disruption, economic pressure, and information manipulation.
The complexity of these emerging threats demands adaptive and comprehensive security architectures. Nations must develop flexible response mechanisms that can effectively address multidimensional challenges spanning technological, economic, and social domains.

Understanding major actors and evolving threats in 2025 requires moving beyond traditional security paradigms. Strategic planners and policymakers must cultivate advanced analytical capabilities, promote international cooperation, and invest in developing robust, adaptive technological infrastructures capable of responding to increasingly sophisticated global security challenges.
Regional Security Complex Theory Explained
Regional Security Complex Theory (RSCT) provides a sophisticated analytical framework for understanding the intricate interactions and interdependencies that shape security dynamics within specific geographical regions. This theoretical approach moves beyond traditional state-centric perspectives, offering a nuanced lens for comprehending how security challenges emerge, evolve, and are managed across interconnected geographical spaces.
Theoretical Foundations and Core Concepts
Developed primarily by Barry Buzan and Ole Wæver, Regional Security Complex Theory fundamentally challenges traditional international relations paradigms by emphasizing the significance of regional interactions. Explore our strategic analysis on regional security frameworks provides deeper insights into these theoretical developments.
At its core, RSCT argues that security dynamics are fundamentally spatial, with regions representing distinct security environments where states interact more intensively with neighboring actors than with distant powers. According to International Studies Quarterly, the theory posits that geographical proximity creates unique security interdependencies that shape strategic behaviors and threat perceptions.
Structural Characteristics of Security Complexes
Regional security complexes are characterized by several critical structural elements. These include patterns of amity and enmity, power distributions, and the degree of security interdependence among regional actors. The theory identifies different types of regional complexes, ranging from highly integrated systems to more fragmented and conflictual configurations.
Key analytical dimensions include:
- Internal Security Dynamics: How states within a region interact and perceive potential threats
- External Security Interactions: Relationships with powers outside the immediate regional context
- Power Configurations: Distribution of military, economic, and diplomatic capabilities
The following table summarizes the core dimensions of Regional Security Complexes and their roles as described above.
| Dimension | Description |
|---|---|
| Internal Security Dynamics | Interaction and threat perceptions among regional states |
| External Security Interactions | Relationships with external powers beyond the region |
| Power Configurations | Distribution of military, economic, and diplomatic power |
| Patterns of Amity/Enmity | Levels of cooperation or conflict within the region |
| Security Interdependence | Degree to which actors’ security is linked within the region |
Contemporary Applications and Analytical Significance
In the contemporary global environment, Regional Security Complex Theory offers crucial insights into understanding complex geopolitical interactions. The approach provides a more nuanced framework for analyzing security challenges that cannot be adequately explained through traditional national security perspectives.
Modern security challenges increasingly transcend simple state-level analyses. Transnational issues like climate change, technological disruption, and economic interdependence require sophisticated analytical approaches that can capture complex regional interactions.
By emphasizing regional interconnectedness, RSCT helps policymakers and strategic analysts develop more comprehensive understanding of security dynamics. The theory enables a more holistic approach to identifying potential conflict zones, understanding strategic alignments, and developing effective regional cooperation mechanisms.
Ultimately, Regional Security Complex Theory represents a critical evolution in international relations scholarship. It provides a robust analytical framework for understanding how geographical proximity, shared historical experiences, and strategic interdependencies shape security environments in an increasingly complex global landscape.
Policy Options and Future Scenarios
Navigating the complex landscape of regional security dynamics requires sophisticated policy approaches that can effectively address emerging challenges and anticipate potential future scenarios. Strategic policymakers must develop adaptive frameworks capable of responding to rapidly evolving geopolitical environments.
Strategic Policy Frameworks for Resilience
Contemporary security policy must transcend traditional defensive strategies and embrace comprehensive, proactive approaches. Explore our strategic policy insights highlights the importance of developing flexible, multidimensional policy mechanisms.
According to RAND Corporation, effective policy options in 2025 will require integrated strategies that simultaneously address technological, economic, and diplomatic dimensions. This demands a holistic approach that connects national security objectives with broader global interconnections.
Key policy considerations include:
- Technological Adaptive Capacity: Developing robust mechanisms for continuous technological assessment and integration
- Collaborative Security Architecture: Creating flexible international cooperation frameworks
- Predictive Intelligence Systems: Implementing advanced analytical capabilities for threat anticipation
Scenario Planning and Risk Mitigation
Future security scenarios are likely to be characterized by increasing complexity and interdependence. Carnegie Endowment for International Peace suggests that policymakers must develop sophisticated scenario planning approaches that can model multiple potential strategic outcomes.
Emerging risk scenarios likely include:
- Hybrid technological warfare
- Transnational cyber disruption
- Complex geopolitical realignments
- Climate security challenges
- Economic network vulnerabilities
Successful policy approaches will require unprecedented levels of interdisciplinary collaboration, integrating insights from technology, economics, diplomacy, and social sciences.
Adaptive Policy Implementation Strategies
Policy implementation in complex security environments demands continuous learning and rapid adaptation. Traditional linear policy development models are increasingly obsolete in a world characterized by rapid technological change and complex interdependencies.
Effective policy strategies must incorporate:
- Continuous scenario modeling
- Flexible response mechanisms
- Robust feedback and evaluation systems
- Interdisciplinary collaboration platforms
Policymakers must cultivate advanced analytical capabilities that enable rapid assessment of emerging challenges and swift, coordinated responses. This requires breaking down traditional institutional silos and developing more agile, interconnected policy ecosystems.
The future of regional security policy lies not in rigid, predetermined approaches but in developing adaptive frameworks that can quickly understand, interpret, and respond to complex, rapidly evolving global dynamics. Success will depend on cultivating institutional flexibility, technological sophistication, and a deep understanding of interconnected global systems.
Frequently Asked Questions
What are the key challenges in regional security dynamics for 2025?
The key challenges include technological disruption, hybrid threats, and the need for adaptive policy frameworks to address complex geopolitical interdependencies.
How is technology impacting regional security dynamics in 2025?
Technology is reshaping security through cyber threats, advanced weapons systems, and new forms of warfare, necessitating comprehensive cybersecurity measures and resilience strategies.
What is Regional Security Complex Theory (RSCT) and its significance?
RSCT analyzes the security interactions and dependencies within specific geographical regions, providing insights into the complex geopolitical dynamics that influence national and regional stability.
How can policymakers effectively address emerging security threats?
Policymakers can address emerging threats by developing flexible, interdisciplinary strategies that integrate technological adaptive capacity, collaborative security architecture, and scenario planning.
Navigate Regional Security Threats With Trusted Geopolitical Expertise
Leaders in security and strategy know the stakes are higher than ever. Are you struggling to keep pace with the rapid rise of hybrid threats, technological disruption, or evolving power dynamics in your region? This article breaks down the latest challenges in regional security dynamics for 2025, from asymmetric warfare to the blurring lines between digital and physical threats. It is clear that old playbooks are no longer enough and you need adaptive insight you can trust.
Take the next step to gain an edge in this complex environment. Dive deeper into proven frameworks, exclusive analyses, and actionable commentary from an authority who truly understands military and geopolitical strategy. Visit Khalid Masood’s homepage for real-world perspectives on emerging security threats and strategic responses to geopolitical uncertainties. Join a community built around deep expertise and stay prepared for tomorrow’s security landscape. Your next breakthrough in strategic understanding starts with khalidmasood.com
Recommended
- Modi’s War Drums Behind the Veil of Celebration: A Stark Warning for Pakistan – khalidmasood.com
- One Big Beautiful Bill Act – khalidmasood.com
- Pakistan’s AD Triumph: Interception of Indian SCALP Cruise Missile – khalidmasood.com
- Chengdu J-20 “Mighty Dragon”: China’s Fifth-Generation Stealth Fighter and Its Strategic Edge – khalidmasood.com
- Top Challenges in Digital Promotion for Local Businesses in 2025 | Ibrandmedia
- Collaborating With Other Consultants: IT Success in 2025







